Der Autor des Artikels: Harshini Anandakumar
Senior IAM Consultant
(Ehemalige Mitarbeiterin)
Role-Based Access Control (RBAC) vs. Attribute-Based Access Control (ABAC)
Access control is a data security process that regulates who can view or access the organisational data. Through authentication and authorization, access control policies make sure users have appropriate access to the company data. Access control identifies users by verifying various login credentials, which can include username and password, security tokens, biometric scans, etc.
Role-Based Access Control (RBAC)
In Role-Based Access Control, users (people) are assigned privileges and permissions based on their roles. It is a policy-neutral access control defined around roles and privileges. The level of access also differs based on roles. The privileges and permissions are set to enable access to authorized users. In other words, an employee should have access to the system and data needed to conduct their daily job, nothing more. This minimizes the risk of an asset being compromised.
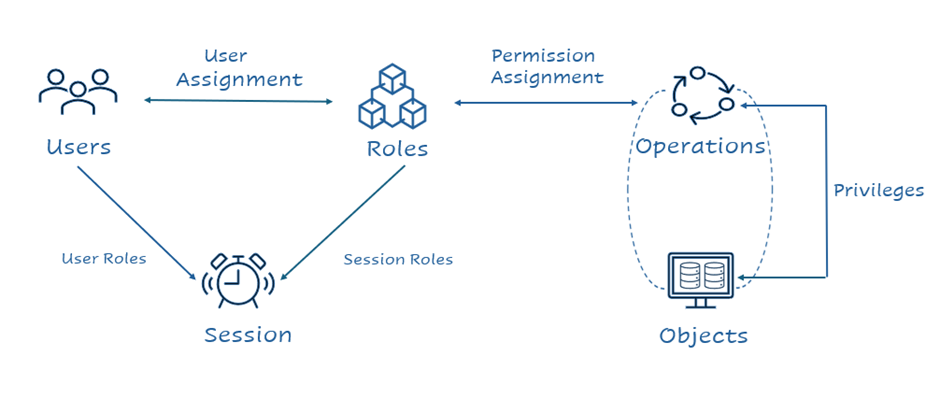
Types of RBAC Model
Role-based access control is divided into four types as follows:
- Flat: All users must have at least one role to accept the permission. Users can be assigned multiple roles to have multiple permissions. All users and permissions are assigned a role.
- Hierarchical: Relationships between roles are set by adding hierarchy to the role structure. Junior role permission is acquired by the higher seniority roles.
- Constrained: Roles are completely separated according to duties so that multiple users can work on the same task, ensuring that no malicious changes can be made to the system.
- Symmetric: Each role associated with permissions is periodically reviewed by the company. Administrators can pull permissions from one user and reassign them to another user.
Example of RBAC
Here are some examples of roles within an RBAC system:
- Chief Technology Officer: Has access to all the servers owned by the organization.
- Software Engineer: Has access to particular application servers.
- Helpdesk Support: Can unlock user accounts and reset user passwords.
- End User: Has basic access to perform day-to-day activities.
Advantages of RBAC
- RBAC allows creating access hierarchies, helping managers to get all the permissions of their direct reports.
- RBAC reduces the risk of unauthorized data access, thus reducing the risk of data breaches.
- Implementing role-based permissions shows the importance of data protection standards, enhancing compliance and making the audit process hassle-free.
- RBAC offers scalability to meet growing demand; its access control can change and evolve as the organizational structure changes.
- RBAC provides flexibility in customizing role definitions and permissions, ensuring organizations of all sizes benefit from robust access control capabilities.
- Administrators can manage roles centrally, making it easier to oversee permissions and ensure consistency across the organization.
Disadvantages of RBAC
- During role explosion, translating business or user requirements into roles can be challenging.
- Administrators keep adding new rules to establish new policies, leading to potential role explosion if not managed properly.
- Implementing RBAC from scratch can be time-consuming, requiring thorough analysis of roles, permissions, and definitions.
- RBAC might be less flexible in dynamic environments due to frequent changes in roles and permissions.
RBAC Best Practices
- Define the resources and data that require limited access, then create roles based on similar access needs.
- Conducting audits guarantees proper adherence.
- Avoid leaving roles unassigned; all created roles must be assigned to users.
- Regularly analyze roles and manage employee access to ensure company security.
Attribute-Based Access Control (ABAC)
Attribute-Based Access Control is an access model that determines access rights based on attributes associated with users, resources, and the environment. This access control provides a flexible and dynamic approach to access management by leveraging a wide range of attributes to define policies. ABAC is also referred to as Policy-Based Access Control (PBAC) or Claim-Based Access Control (CBAC). Compared to other access mechanisms, ABAC is dynamic and much more context-aware of the environment conditions in which it operates.
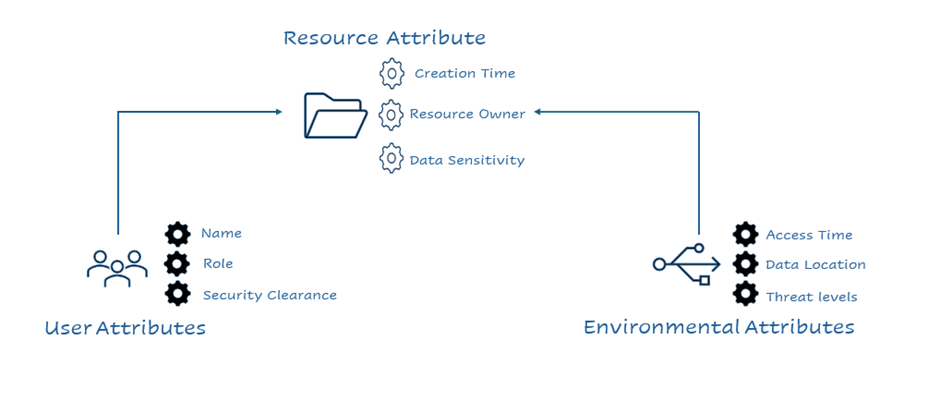
Example of ABAC
A simple example of ABAC: All employees can read public data in an organization. You can also use an ABAC policy to enforce that only admins can edit public information of the organization during working hours.
Advantages of ABAC
- Authorization for data or applications can be dynamically assigned or revoked in real-time since ABAC is attribute-based.
- Encapsulation is used in ABAC to hide technical permissions in plain sight.
- ABAC allows very specific and detailed access control policies based on a wide range of attributes.
- By leveraging a combination of attributes, ABAC can manage a vast number of users and resources without creating numerous roles.
- Policies are managed based on attributes rather than manually managing individual permissions or roles by administrators.
ABAC Disadvantages
- Designing and implementing ABAC is complex and time-consuming. Defining attributes requires significant time and resources, in addition to creating the accompanying policy engine.
- Attribute management does not scale easily due to configuration challenges when managing hundreds or thousands of users.
- Identifying and resolving issues or conflicts with ABAC is more difficult compared to simpler access models.
- Regular updates and maintenance of attributes and policies are required to ensure they remain relevant and effective.
- With many policies, there is a risk of overlap and conflicts, complicating policy administration and access control decisions.
ABAC Best Practices
- Establish the business case by defining ABAC costs, benefits, and risks.
- Understand operational requirements and the enterprise's overall architecture.
- Establish refined business processes to define ABAC, such as access roles and policy documentation.
- Develop interoperable capabilities that facilitate integration with identity management and oversee unique identities.
- Evaluate performance by managing subject attributes and measuring the quality and timeliness of changes.
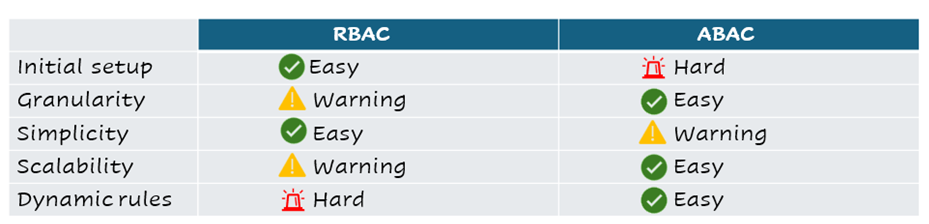
RBAC vs ABAC
| Features | RBAC | ABAC |
|---|
| Access Grant basis | Predefined roles | User attributes, Resource attributes, and environment factors |
| Complexity | Simple. Easy to implement | Complex. Resource-intensive implementation |
| Role Update | Manual | Automatic |
| Flexibility | Less flexible | More flexible. Adaptable to specific contexts |
| Cost | Lower | Higher |
| Integration | Easier integration with existing systems | Requires integration with additional systems |
| Granularity | Limited. May lead to role explosion | Highly granular, dynamic permission |
| Best Suited for | Small to medium organizations with well-defined roles | Large organizations with complex access needs |
| Data Source | Roles | User information, resource attributes, and environment factors |
| Security | Moderate | Potentially higher due to granular control |
| Hybrid Model | Can be combined with ABAC for comprehensive control | Can be combined with RBAC for simpler management |
Guidelines for choosing the right access control model based on organizational needs:
After exploring the advantages and disadvantages of RBAC and ABAC, one may wonder which is the best access control for their organization.
Below are some use cases that need to be considered.
- The key difference between RBAC and ABAC lies in how access permissions are granted.
- For an organization distributed across multiple locations, ABAC is a better choice. Granting permission based on the location of employees and allowing access only during business hours can be easily achieved by implementing ABAC.
- It is easier to define permissions according to roles when the organization is small with few resources and team members; using the RBAC approach can be more efficient.
- When teams working temporarily on a project need access to sensitive documents and systems during office hours, using an ABAC system can be beneficial. The time-based rule prevents access to sensitive documents and data when it is not needed, thus preventing data breaches.
- ABAC provides a much deeper approach, allowing you to add attributes into the mix, which allows for more dynamic access control. However, ABAC can consume more processing power and implementation time, requiring a balance in the authorization policy.


